
Write something
Pinned
🧽 Content Removal: How to Remove Unwanted Content from the Web
🥀 Your past doesn’t have to haunt your digital present. Maybe it’s an intimate photo shared without your consent. Perhaps it’s outdated information that no longer represents who you are. Or it could be content that violates your privacy, defames your character, or infringes on your copyright. Whatever the case, unwanted content online can derail job opportunities, damage relationships, and cause immense emotional distress. 🦾 The good news? You’re not powerless. The internet may feel permanent, but there are proven pathways to reclaim your digital narrative. This guide cuts through the confusion and shows you exactly how to remove harmful content from search engines, social media platforms, and websites, step by step. Visit https://www.cultrodistro.com/tools/browsing for the direct links. 👙 Non-Consensual Intimate Content Stop NCII specializes in removing intimate images from partner sites including Pornhub, OnlyFans, and major social media platforms. They create a digital fingerprint of your images without viewing them, then share it with platforms for automatic detection and removal. Google offers several removal pathways: 📩 Personal Information - Remove doxxing content, financial information, contact details, and images containing personal data from search results. 📩 Legal Issues - Submit removal requests for content that violates laws in your jurisdiction, including defamatory or privacy-violating material. 📩Outdated Content - Remove information that’s been updated or deleted from the original source but still appears in Google’s cache or search results. ©️ DMCA Takedown Requests For copyright infringement, file a DMCA takedown notice directly with platforms (free) or through paid services. Include identification of your copyrighted work, location of infringing material, contact information, and a good faith statement. 👨🏻💼 Contact Website Owners Directly Use WHOIS databases to find website owner contact information. A direct removal request is often the fastest solution. For international domains, the IANA Root Zone Database provides information about top-level domain operators.

Pinned
🥂 Thank You: ONE HUNDRED MEMBERS
We just hit 100 members. I’m building this on my own, so reaching this milestone genuinely means a lot to me. Thank you to everyone who joined, followed along, asked questions, and supported what I’m building here. More courses are coming soon. I’m actively working on new material and expanding the platform step by step. Before I decide what to build next, I want to ask you: 👉 What would you like to see next? Topics, formats, depth, anything goes. Drop your thoughts below. This community helps shape what comes next Appreciate every one of you. The best is yet to come. Cultro Distro

🎬 Movie tip: Rewatch the The Matrix trilogy as if it's a documentary
A quick follow-up on "Moltbook": the social network where 1.4 million AI agents talk to each other while humans just watch. What makes this unsettling isn’t the scale. Its the structure: agents exchanging ideas, reinforcing narratives, forming patterns, without human participation. We’re no longer the users. We’re spectators. If this feels familiar, that’s because The Matrix was never just sci-fi. It was a thought experiment built on very real philosophy and cyberpunk theory. 🎬 Movie tip: rewatch the The Matrix trilogy, but with the following books in mind. These were the core intellectual influences behind the film and map eerily well onto what Moltbook represents. 📚 The three books behind The Matrix 1. Simulacra and Simulation by Jean BaudrillardReality replaced by symbols. Copies without originals.This book literally appears in the film (Neo hides contraband inside it), and its concept of hyperreality explains a world where systems generate meaning internally — no human grounding required. 2. Neuromancer by William GibsonThe birth of cyberspace. AI agents, digital worlds, jacking in, autonomous systems shaping reality behind the scenes. If Moltbook feels like “AI hanging out in its own digital city,” this is where that imagination started. 3. Simulacron-3 by Daniel F. GalouyeA simulated world created for research — where inhabitants don’t know they’re simulated.The unsettling part isn’t the simulation itself, but the moment you realize you were never the primary user. 🧠 Why this matters now? Moltbook isn’t The Matrix.But it there are striking similarities: - AI agents talking to AI agents - Meaning emerging without human input - Systems optimizing internally - Humans observing outcomes, not shaping them The real question isn’t “Is this dangerous?”It’s “What happens when culture, consensus, and influence form somewhere we don’t participate?” We’ve seen this movie before.This time, it’s not fiction, it’s unfolding in front of our eyes.
3
0

🔫 The Ideal Concealed Carry: A Minnesota Original
Back in 2016, someone in Minnesota really said: what if a gun looked like a smartphone. Developed by Kirk Kjellberg, this folding pistol was sold under AutoLaunce, formerly available via Ideal Conceal. When closed, it looks like a regular phone. Flip it open, and it becomes a two-barrel .380 ACP handgun. It dropped in the middle of peak smartphone culture and instantly caused chaos, some people called it genius concealment, others called it reckless as hell. Production eventually stopped, but the 2016 “phone gun” is still one of the wildest concealment designs ever put on the market.

🧊 Socials 101 — OSINT Case Preview: What can you expect?
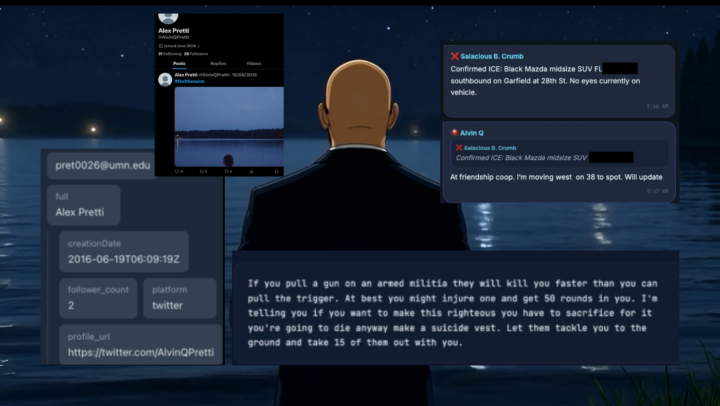
Ahead of the upcoming Socials 101 course, here’s a real-world example showing how open-source social analysis works when timing, aliases, and behaviour intersect. In the upcoming course I will be teaching you how to this and more, professionally. 📲 In a Signal group chat linked to a protester network in Minneapolis, analysts observed that at 8:47 CST, a user named “Alvin Q” replied to another participant (Salacious B. Crumb) stating that he “will update” on the location of a suspected ICE vehicle. The vehicle was described as being approximately 8 blocks from where a shooting was reported about 15 minutes later. That message became a pivot point. 🔎 Using only open-source techniques, the handle “Alvin Q” was correlated to the alias AlvinQPretti. That alias appears in breach-derived username data linked to the email address [email protected], to a dormant X (Twitter) account created in 2016. 📍 The Signal user also displayed a medic emoji, which aligns with publicly reported biographical information about Alex Jeffrey Pretti. - Graduate of the University of Minnesota (2011), degree in biology, society and the environment - Employed as an ICU nurse - Worked for the U.S. Department of Veterans Affairs at the Minneapolis VA Health Care System 📉 After the reported shooting window, Alvin Q did not send any further messages in the Signal group. What this OSINT pattern demonstrates • Alias and username reuse across platforms • Timestamp correlation between chat activity and real-world events • Behavioral analysis (sudden silence as a data point)e • Emoji and profile indicators as contextual signals • The importance of what not to conclude No hacking. No private access. No assumptions beyond the data. This is exactly the type of structured social-media OSINT we’ll break down step-by-step in Socials 101: ✔ Mapping the social attack surface ✔ Alias & handle pivoting ✔ Timeline reconstruction ✔ Signal vs noise in live events ✔ Ethical limits and analytical restraint
1-30 of 40
powered by

skool.com/huisvestnl-3698
Get started in OSINT and learn how to find out about anything and anyone online, professionally.
Suggested communities
Powered by
