Activity
Mon
Wed
Fri
Sun
Jan
Feb
Mar
Apr
May
Jun
Jul
Aug
Sep
Oct
Nov
Dec
What is this?
Less
More
Owned by Bobby
Run secure, reliable IT in‑house with SOPs, vendor scripts, and live office hours. Cancel anytime. 30‑day “love it or don’t pay” guarantee.
Memberships
7 contributions to The IT Club
Your Network Is Only as Secure as Its Weakest Device
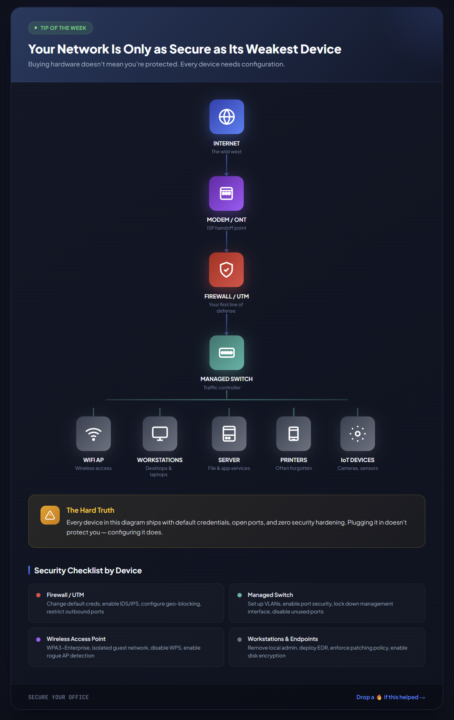
🔒 TIP OF THE WEEK: Your Network Is Only as Secure as Its Weakest Device Here's something most small business owners don't realize: Buying network equipment doesn't mean you're protected. That firewall you just installed? It shipped with default credentials (admin/admin), all outbound ports open, and zero threat detection enabled. That shiny new WiFi access point? WPS is on, there's no guest isolation, and it's broadcasting on the same network as your accounting server. What Every Office Network Should Look Like I put together a visual showing the basic flow of a properly structured network: Internet → Modem/ONT → Firewall → Switch → Endpoints Your endpoints branch off from the switch: WiFi access points, workstations, servers, printers, and IoT devices (cameras, sensors, etc.) Simple enough. But here's the catch: every single one of those devices needs specific security hardening. Quick Security Checklist by Device 🔴 Firewall / UTM - Change default credentials immediately - Enable IDS/IPS (Intrusion Detection/Prevention) - Configure geo-blocking for countries you don't do business with - Restrict outbound ports (block everything except what's needed) 🟢 Managed Switch - Set up VLANs (separate guest, IoT, and production traffic) - Enable port security - Lock down the management interface - Disable unused ports 🟣 Wireless Access Point - WPA3-Enterprise if possible, WPA2-Enterprise minimum - Create an isolated guest network - Disable WPS (it's a known vulnerability) - Enable rogue AP detection ⚫ Workstations & Endpoints - Remove local admin rights from daily users - Deploy EDR (Endpoint Detection & Response) - Enforce automatic patching - Enable disk encryption (BitLocker, FileVault) ⚫ Printers & IoT - Change default passwords (yes, printers have admin panels) - Update firmware regularly - Isolate on their own VLAN - Disable unnecessary protocols (FTP, Telnet, SNMP v1/v2) The Bottom Line Network security isn't a product you buy. It's a process you implement.
0
0
Why I’m Loving Ninite (and you should too)
If you’ve ever set up a new PC, rebuilt a machine for a client, or just gone through the slog of “install this → next → agree → install that → reboot → repeat”, then you’ll appreciate this: Ninite takes that pain away. What Ninite is: Ninite is a web-based service for Windows where you pick from a list of popular software, download a single custom installer, and let it run. It installs (or updates) all chosen applications automatically, in the background. TechBloat+3How-To Geek+3PC Tips+3 Why it’s awesome compared to manually downloading each app: - Time saver: Rather than visiting dozens of sites, clicking through multiple installers, dealing with extra toolbars or adware, you just pick your apps once and let Ninite handle the rest. Tech Reda+1 - Clean installs: It avoids bundling unwanted third-party toolbars or junk. It “says no” to toolbars and extra junk. Ninite+1 - Always grabs latest versions: When you run the same installer again, it updates apps that are out of date and skips the ones already current. How-To Geek+1 - Ideal for IT pros / MSPs: For someone like you (with an MSP business), when you’re provisioning many machines, this becomes a big productivity boost. Automating installs = less manual effort, fewer mistakes. Tech Reda+1 - Trusted source: It downloads directly from official sites and verifies digital signatures/hashes before running. As you set up new client machines, or refresh workstations after OS reinstall, create a “base image + Ninite installer” routine. One click, boom: your standard set of browsers, productivity tools, utilities are installed cleanly. Fewer clicks, fewer support tickets for “why is this toolbar showing up”.
2
0

Cyber-Security Tip of the Week
⚠️ Be Careful with Microsoft Phone Link — It’s Becoming a Major Attack Vector I want to call attention to something that’s flying under the radar for a lot of users and businesses: the Microsoft Phone Link app (formerly Your Phone). It’s a great productivity tool when used properly, as it lets you view messages, notifications, and photos from your Android phone (and even available now on iOS) Windows PC. But it’s also become a growing security concern. Here’s the problem: bad actors are now using this same convenience to their advantage. They’re tricking users (often through remote support scams or fake IT calls) into connecting a virtual or attacker-controlled phone to the victim’s computer using Phone Link. Once connected, the attacker can: - Receive MFA (multi-factor authentication) codes meant for the real user. - Access texts or notifications that contain password resets or verification codes. - Leverage access to other apps (like Outlook, Teams, or banking) that rely on SMS or app-based authentication. Because Phone Link operates within the user’s own Microsoft account, these attacks can slip right past normal endpoint protection tools. It looks like a legitimate connection. What to Watch For: - Never approve a Phone Link pairing unless you initiated it. - If someone “helping you” (even claiming to be from Microsoft or your IT provider) asks you to scan a QR code in the Phone Link app — stop immediately. - Check Settings → Bluetooth & Devices → Mobile Devices in Windows to see if an unfamiliar phone is connected. Remove anything you don’t recognize. - Use app-based MFA (like Microsoft Authenticator or Duo) instead of text-message codes whenever possible. - If you suspect compromise, disconnect the phone, reset your Microsoft account password, and contact your IT team. Technology designed for convenience often becomes a backdoor for exploitation when awareness doesn’t keep up. Microsoft Phone Link isn’t inherently bad, it’s just being misused by increasingly clever attackers.
Weekly IT News & Insights
This category is our Weekly IT News & Insights thread. The goal is simple: every week, we share the IT news, updates, or trends we’re seeing and discuss what it actually means for small businesses. Here’s how to use it: 1️⃣ Post the IT stories, changes, or rumors you’ve heard (security alerts, Microsoft updates, vendor changes, compliance news, etc.). 2️⃣ Share your thoughts or questions. Don’t worry if you’re not sure, that’s the point. 3️⃣ Jump into the conversation! Add your perspective, lessons learned, or how you’d handle it. This is where we sharpen each other, spot risks before they hit, and make sure no one here gets blindsided by tech chaos. Let me know if anything’s unclear.
1
0
Starter Pack - Downloads Here:
Most business owners, office managers, and practice administrators don’t think about IT until something breaks. That’s the worst time to figure it out. These downloads are the cheat codes. They show you exactly what to do when “that” scenario happens, whether it’s downtime, security, or the random tech chaos that halts your business. Use them to make decisions faster, avoid costly mistakes, and know you’re covered when the unexpected hits. No theory. Just plug-and-play resources you can actually use. (.docx files so you can edit as needed)
1-7 of 7
@bobby-boykin-1296
Founder @ FIRN Services | Making IT simple, strategic & growth-focused. I help private healthcare practices stay secure with super-smart tech stuff.
Active 3d ago
Joined Aug 19, 2025
ENFJ
Fort Worth, TX
Powered by

