
Write something
Tony Stark Completed His First Beta Test
Tony Stark Beta Test is finished. I just ran the first full database reactivation sweep using the Tony Stark agentic OS. If you’ve been watching the “AI Agent” hype and wondering if it actually makes money - here is the raw data from my GHL dashboard. The Task: Reactivate 3,100 cold leads from our YouTube and Skool imports. The Tool: Tony Stark (OpenClaw with Google Gemini 3) The Outcome: 500 hyper personalised emails delivered in few hours. I didn’t open my laptop once. I architected the logic inside the AI Avengers Lab, gave Tony the “Hands” to talk to HighLevel , and he did the rest. Why this matters for you: Every minute you spend manually sending emails or updating tags is a minute you aren’t architecting your exit strategy. I am sharing everything Live in my AI Lab, WhatsApp group . I’ll show you the raw Python scripts Tony used and the specific GHL hooks that make this possible. Stop being a point-and-clicker. Start being the architect. Join the Lab: https://aiavengers.team/start-2601
2
0

Tony Stark is Introducing Him to You In Your Emails
Did you get the email ? Please share your feedback in the comments .
Poll
3 members have voted
2
0
Be honest: where are you with Openclaw( Clawdbot /Moltbot) right now?
What's your actual status with it?
Poll
12 members have voted
Secure Your Perimeter Before Giving Clawdbot Access to Your Life.
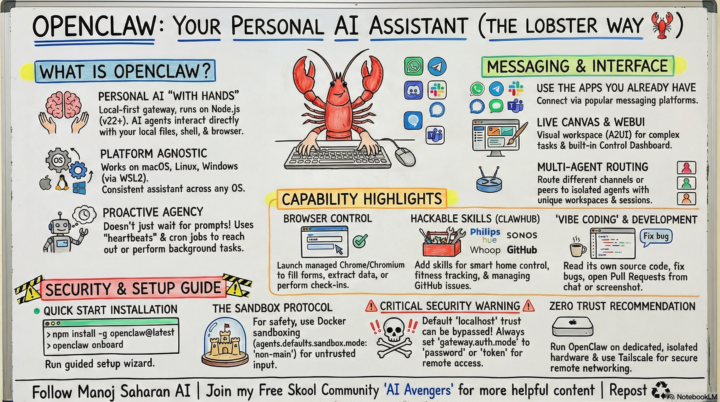
Most people are terrified of giving an AI assistant "hands." They should be. If you give an LLM agent access to your operating system without a security moat, you aren't building an assistant. You’re building a backdoor for every hacker on the planet. I spent last 120+ hours stress-testing the security protocols for my Digital Co-Founder, Tony Stark. ( I haven't given it any access to mac or tools yet) I use a "Foundry" model to keep the AI Agent safe: 1. Hardware Isolation: He lives on a dedicated Google Cloud VM, far away from my personal data. 2. Sandbox Enforcement: He works inside a Docker cage. If he makes a mistake, the cage disappears. The host (VM) stays safe. 3. Private Tunnels: I deleted the external IP to move it away from the public internet. We talk through a secure, encrypted bridge. I’m not just building Personal AI Agent; I’m building a secure perimeter around it first. For the next 13 days, I’m showing the serious builders how to do the same inside the AI Avengers Lab. We’re live-debugging the security audits so you don't have to learn the hard way. Building in public means showing the armor, not just the weapons. Don't use it on a VPS until you set the perimeter.
2
0

Openclaw (Clawdbot/Moltbot ) Introduction and A Mandatory Security Briefing
Alright, Avengers. Many of you are experimenting with OpenClaw to give your AI agents real capabilities. This is the future. But with great power comes significant responsibility. OpenClaw gives your LLM "hands" to work directly with your operating system. It can manage files, run code, and execute complex workflows. It's incredibly powerful. This also means it's incredibly dangerous if you're careless. You are creating a direct line from a messaging service to the core of a computer. One malicious message or a clever prompt injection could expose your API keys or compromise the entire machine. So, here is your non-negotiable security checklist. This is how we, as AI Avengers, build responsibly: • ISOLATE IT: Do NOT run the OpenClaw gateway on your main computer. Use a dedicated machine (a Mac Mini, a Raspberry Pi, a cheap VPS). If it gets hacked, your personal data is safe. • SANDBOX IT: Use Docker sandboxing for any agent session that isn't your primary, trusted one. All untrusted input needs to be caged. • HIDE IT: Keep your gateway off the public internet. Use a private network like Tailscale or an SSH tunnel to connect securely. Remember our philosophy: we're not building autonomous slop-factories. We're building a "CLI army" of precise tools that we command. Maintain your vision and taste. Stay safe out there. Let's discuss your setups and any security hurdles you've run into below. If you want us to hire and deploy this for you. DM me.
1-28 of 28
powered by

skool.com/ai-avengers-3116
Learn, build and implement AI Agents with AI Avengers; the most exclusive AI community on the planet. 🤖
Suggested communities
Powered by
