Activity
Mon
Wed
Fri
Sun
Mar
Apr
May
Jun
Jul
Aug
Sep
Oct
Nov
Dec
Jan
Feb
What is this?
Less
More
Memberships
Grey Man Academy
54 members • Free
The Grim Circle
1.2k members • $39/m
11 contributions to Grey Man Academy
NEW RESOURCE DROP: Grey Man Combatives Level 1 Training Manual
Here's a short announcement post for your Skool community: 🎯 NEW RESOURCE DROP: Grey Man Combatives Level 1 Training Manual Team, Just finished developing something special for this community - our complete Grey Man Combatives Level 1 Training Manual. This isn't some watered-down PDF. This is the abbreviated version of the same curriculum we use in our $8,000 three-day intensives at Serenity Houses. What's inside: - The 6 Rules for Effective Striking (miss one = failure) - 12 four-strike practice sets with detailed breakdowns - Competition vs. Combat mindset training - Legal/moral framework for justified force - Advanced techniques section (joint breaking, additional tools) - Safety protocols that keep you training, not recovering This manual represents decades of SERE expertise distilled into actionable training methodology. The same principles that keep executives alive in high-risk environments worldwide. Why am I sharing this here? Because this community gets it. You understand that being your own first responder isn't paranoia - it's preparation. Strategic invisibility with lethal capability isn't a tagline - it's a lifestyle. Download it. Study it. Train with it. But remember - reading doesn't replace training. If you're serious about mastery, you know where to find us. Stay dangerous, Stand ready and be prepared! Michael P.S. - This manual is exclusive to our Skool community. Treat it accordingly. Also find it in the classroom section for future reference.

Why the Ghost Protocol Checklist Is Essential in Our Connected World
In an era where data breaches make headlines weekly and digital surveillance has become ubiquitous, the question isn't whether you need robust digital security—it's whether you can afford not to have it. The Ghost Protocol Checklist, developed through collaboration between multiple branches of military intelligence and isolated personnel specialists, represents a paradigm shift in how we think about digital security: not as an IT checkbox, but as a fundamental survival skill. What makes this guide extraordinary is its pedigree. Born from the real-world experiences of military intelligence operatives and specialists who train personnel to survive in isolation and hostile conditions, these protocols have been battle-tested in the world's most dangerous environments. Now, this classified-level tradecraft has been adapted and made accessible for everyday citizens—transforming military-grade operational security into practical protection anyone can implement. Military Intelligence Meets Civilian Protection The Ghost Protocol's development involved input from professionals who have spent careers protecting the most vulnerable and high-value personnel in the most dangerous conditions imaginable. Military intelligence branches understand adversarial thinking—they know how hostile actors identify, track, and exploit targets because they've studied these tactics at the highest levels. Isolated personnel specialists train servicemembers to survive capture, resist exploitation, and maintain operational security under extreme duress. This convergence of expertise produces something remarkable: a security framework that assumes the worst-case scenario and builds protection accordingly. The protocols don't hope your security holds—they assume it will be tested by sophisticated adversaries and ensure you have backup systems, escape routes, and contingency plans at every level. What makes the Ghost Protocol revolutionary is that this military-intelligence-grade protection has been declassified and adapted for civilian use. The same techniques protecting special operations forces, intelligence officers, and isolated personnel in hostile territories are now available to protect business travelers, digital nomads, journalists, activists, and anyone who recognizes that digital security is no longer optional in our connected world.

The Need for Proactive Courses Of Action in a Dangerous World
When Time = Life then Hesitation Kills. We live in an ever-increasing dangerous world. A world where kids are getting picked up from streets once thought safe, and more and more frequently we hear of another school, church or other “Mass Shooting Incident”. It is a hard truth to accept that our own safety is not simply a factor of how we live. We can often mitigate how much danger we incur as a whole, simply by not doing Stupid things, with Stupid people at Stupid times in Stupid places. However, as many innocent victims in recent crime statistics will tell you, you can do everything right and still be targeted by villains. And life-threatening danger, like it or not, can always knock on our door. Even without ever interacting with criminal elements, far too many people are affected by roadway accidents, or injuries at work where conditions and our local environment seem to have it out for us. Something as innocuous as falling off a roof or slipping from a ladder has shattered the lives of some that could have been mitigated if more people would have Proactive COA’s. According to the Military a COA is; Definition: Course of Action (COA) In incident-level decision making, a Course of Action (COA) is an overall plan that describes the selected strategies and management actions intended to achieve Incident Objectives, comply with Incident Requirements, and are based on current and expected conditions. What is a Proactive COA? Example listed below. It is definable action taken, if/when something happens. A Course Of Action that is preestablished so that you act with intentionality. Specific and timely actions that do not necessitate prior thought. If A, then B. If as in this example, you see someone who’s unmistakably an operator while on the run, (and you happen to be a Navy SEAL commander that’s been targeted as the fall man for a criminal ambush of several US service members) then it’s not time to consider what to do. It’s simply a time to act. Namely, confront said individual in a way that reveals his true identity.
3 likes • Oct '25
Thank you again! In my training, constant awareness was emphasized. Not just as a "survival tool", but just as a way of life. In the color chart you described previously, in my opinion, there is really should be no such thing as a "white color". I think one can be absolutely relaxed and yet still aware. Interestingly, when I am working with native elders and healers, this is exactly what teach as well. Relaxed, no tension and yet aware of every detail. It is actually liberating. As well as helpful:)
Preparedness Bag Selector Interactive Tool
https://claude.ai/public/artifacts/6f78a088-195f-4aa2-a771-2e5237dcbb65 Guys, please give me some feedback on this. Here's the backstory on this. I recently wrote a couple of small articles on what are standard gear bags, (WUSH, Get Home Bag, Bug out Bag, INCH bag) each has a specific purpose and I've found that often these bags get mixed up. Someone who wants to be prepared will throw some gear into a bag, perhaps keep it in their vehicle "just in case" but few have a very narrowly defined purpose for a particular gear bag, and fewer still have methodically thought about each and every piece of gear from a principled perspective. (Considering their most likely scenario, most likely duration, physical limitations, environmental conditions etc.) To help with this, I've been working on this interactive tool, which not only guides users into thinking critically on which type of bag is right for them. But also exactly what should go into it for their specific application. It's a work in progress. There's a suggested list of items at the end, but I still need to refine the output significantly. Please use this, tell me if it was helpful for you, and how I might improve it for others.
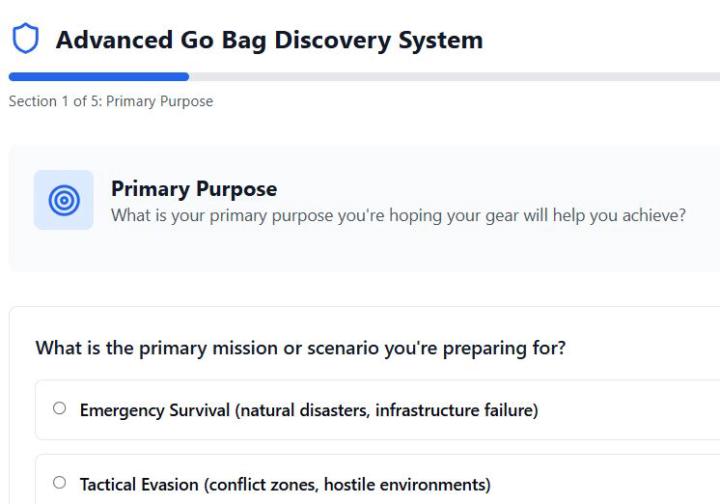
2 likes • Sep '25
Tool is working. I did like it as a step one. For most emergency situations, still consideration of hostile forces (or people wanting to share what you have) and stepwise approach should be clarified (I think). It is amazing to me how often people I am talking to, despite of evidence and stories relying of "them" to come and save/feed/protect/treat me.
The Anatomy and Purpose of Essential “Go Bag” Types: WUSH, EDC, Get Home, Bug Out, and INCH Bags
In an unpredictable world, preparedness has become a central tenet for individuals and families alike. One manifestation of this preparedness ethos is the well-packed “go bag”—a portable collection of essential items ready for immediate use in various situations. Over time, distinct types of go bags have evolved to suit different scenarios, each with a specific function and set of contents. This article unpacks five key go bag types: the Wake Up, Shit’s Happening (WUSH) Bag, Every Day Carry (EDC), Get Home Bag, Bug Out Bag (BOB), and I’m Never Coming Home (INCH) Bag. By understanding their purpose and appropriate contents, you can build a comprehensive readiness plan tailored to your needs. 1. Wake Up, Shit’s Happening (WUSH) Bag Purpose: The WUSH bag is designed for immediate, unexpected emergencies—those moments when you wake to sirens, alarms, or chaos and have seconds to act. It is a minimalist, grab-and-go solution, focusing on survival essentials for the first few minutes or hours after a crisis begins. While many people’s normal lives don’t require having this in place for every day application at their primary domicile, I recommend this to always be in place when traveling away from home. Make-up: The WUSH bag’s defining feature is speed and simplicity. It is often a small bag or pouch—compact enough to be kept at your bedside, under your bed, or hanging on a doorknob. The contents are intentionally limited, aimed at helping you escape imminent danger and reach your next safety checkpoint. · Identification and Documents: Photocopies or waterproofed originals of IDs, emergency contacts, medical info, etc. · Keys: Car, and any critical access keys, possibly on a breakaway lanyard. · Cash/Card: Small denomination local currency for immediate needs (payphones, transport, food). · Flashlight: Preferably super bright, or a headlamp for hands-free use. · Potentially with Basic Clothing: A sturdy pair of shoes, socks, weather-appropriate outerwear, and hat.
3 likes • Sep '25
Maybe small bit that I do not see recommended too often. "Comfort" item. Something small, light, personal but what makes your mind to relax. Anything from favorite music (bring your headphones, others in your team may not appreciate your choices or just noise, everybody is tired :) ), book, actual or audio, small music instrument. Whatever may bring your mind away from the current events. Some of these can be quite traumatic and one cannot be just in a survival mode all the time. Heard a phrase form one of the WWII veterans that stuck with me: "war is not only a fight, but it's also life". Sorry, difficult to translate directly. Goes along with my army sergeant saying: "we are not trying to just survive, we are living".
1-10 of 11
Active 21d ago
Joined Aug 28, 2025


