Activity
Mon
Wed
Fri
Sun
Jan
Feb
Mar
Apr
May
Jun
Jul
Aug
Sep
Oct
Nov
Dec
What is this?
Less
More
Memberships
Cyber Guard Academy
63 members • Free
7 contributions to Cyber Guard Academy
🚀 Challenge Time: Build Real Cybersecurity Skills with 20 Hands-On Projects
Hey everyone 👋 If you’re serious about becoming a SOC Analyst or Cybersecurity Professional, this is your chance to build real hands-on experience not just theory. I came across this awesome list of projects that help you practice real SOC skills: 🔗 20+ Hands-On Cybersecurity Projects That Will Get You Hired – Undercode Testing Here are a few ideas to start with 👇 - 🧠 Password Strength Tester (Python) - 🔍 Simple Vulnerability Scanner (Nmap + Bash) - 🧩 File Integrity Monitoring - ⚙️ Wazuh SIEM Setup - 🧑💻 Network Traffic Analysis (Wireshark/Zeek) - 🛡️ IDS/IPS Setup (Snort/Suricata) - 🚨 Incident Response Simulation (TheHive + Cortex) - 🌐 Threat Intelligence Dashboard (MISP + Elastic) - 🔒 Security Onion Monitoring Lab 💪 How to get the most out of this: 1) Pick one project from the list. 2) Set up your lab environment and start experimenting. 3) Document everything — screenshots, what you learned, and results. 4) Post your progress here so we can all learn together. 5) Add it to your GitHub or resume — show real, practical experience. Let’s make this a mini-challenge 🔥 Drop a comment below with which project you’re starting and what tools you’ll use. We can help each other troubleshoot, share results, and grow together 💻🛡️
What’s your biggest frustration with your job search so far?
- Are you struggling with the lack of responses, confusing job requirements, or constant rejections that don’t give real feedback? - Do you feel like the hiring process has become messy, slow, or flat-out inconsistent? - What’s one thing you wish companies would fix to make the process fair and actually useful for candidates? Drop your answer below. Someone else in the group is dealing with the same thing, and your perspective might help them.
2 likes • 9d
It would be GREAT if any job was based on merit. As we all know, networking is key when it comes to getting a job, and there are a lot of people in positions based on who they know not what they know and are capable of. All of the above. I feel that the hiring process has become slow and flat. I agree with Nick, there is no way to respond and find out what you're missing or not missing.
What’s the toughest cybersecurity interview question you’ve ever been hit with?
For me, the one that really made me pause was: “Tell me about the worst incident you handled. Walk me through what you did from the moment it started until it was resolved.” It wasn’t about theory. They wanted to see how I actually think when things get messy, how I break down an investigation, and where my real hands on experience shows up. Now I’m curious! - What question caught you off guard or made you stop and think? Drop yours below.
1 like • 9d
Here is a good one... well, it was something like this: “You’re the only analyst on shift. EDR just flagged possible ransomware on a critical file server that supports patient care. Walk through exactly what you do in the first 15 minutes. What do you touch, what do you NOT touch, who do you call, and what tradeoffs are you considering?” There was another variable regarding having to leave work on time too, it was thick. I think I sustained a TIA during the question.
Have You Ever Built a Home SOC Lab? What Tools Did You Use?
I’m curious how everyone here puts their labs together. Some people keep it simple, others go all-in with a full mini-SOC at home. If you’ve built a SOC lab before, what did you use? - What SIEM did you go with? - Any EDR tools you liked? - Local VMs or cloud? - Any open-source tools you swear by? - Screenshots or setups you want to show off? Share whatever you’ve got. It helps the whole group see different approaches and maybe pick up a few new ideas.
Phishing Scams Are Getting Smarter. Have You Seen Any New Tactics Recently?
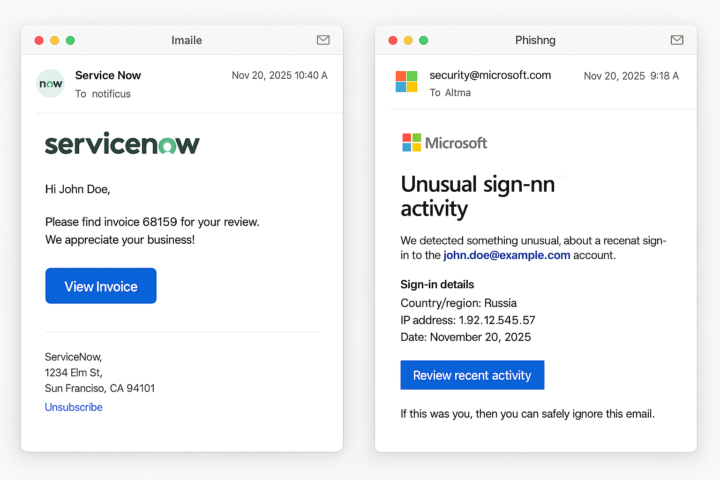
Attackers are not using the same obvious scams anymore. They are getting cleverer. Their tactics are more personalized and more convincing. Some of the new attempts look nearly identical to real vendor emails, MFA prompts, or internal notifications. I want to know what you are observing. Share the strange ones, the convincing ones, and the scams that nearly caught you or your team. Just remember to remove any sensitive information before posting. - Fake MFA push floods - AI-generated emails that sound very real - Spoofed HR or payroll updates - Fake password-reset notifications - QR code phishing - Deepfake voice or video attempts - Any new method attackers are using The goal is to help everyone stay informed about what is really happening. If you’ve noticed something new or surprising, please share it below. Quiz for today? - I posted two email screenshots. One is real. One is a phishing attempt. - Your job is simple. Tell me which one is legitimate and which one is fake, and explain why you think so. Drop your answer below. Let’s see who can spot the red flags fastest.
1-7 of 7
@jon-brendese-9615
Passionate cyber grad with a specialty in Cyber Ops. Skilled in Tenable, QRadar, Splunk, SentinelOne, AWS, Proofpoint, Python, Kali, Wireshark.
Active 1d ago
Joined Nov 9, 2025
Albany, NY


