Activity
Mon
Wed
Fri
Sun
Mar
Apr
May
Jun
Jul
Aug
Sep
Oct
Nov
Dec
Jan
Feb
What is this?
Less
More
Memberships
The Cyber Pros
864 members • Free
GC
Growthworks Community
24.1k members • Free
Start Writing Online
19.8k members • Free
6 contributions to The Cyber Pros
Good afternoon
Hi everyone, I am new to the world of cybersecurity! I recently passed my CompTIA Sec+ exam this past week. I am excited to learn more and dive into the industry!
Things to look for in cybersecurity trainings.
Ok need some thoughts on cybersecurity training programs. Backstory: I'm currently pivoting from my current career into cybersecurity. In the last 2 weeks I've come across a cybersecurity training program (who shall remain nameless) they were offering a 3 month program, 7 certs: COMPTIA A+, EC council C|EH, security+, CASP+ Cybersecuriy fundamentals (I believe IASCA but don't quote me) NIST RMF (which immediately sent up red flags) I don't think NIST RMF is a cert. I believe the industry cert is the ISC2 CGRC. And STIGS (Again, I don't believe this is a cert). The program also came with the hands on labs. They quoted me $20,000 USD! I know I'm new to cybersecurity but 20K seems ridiculous! Especially given that some of the "certs" they're offering aren't really certifications recognized by the normal certifying bodies. What do you guys think?
1
0
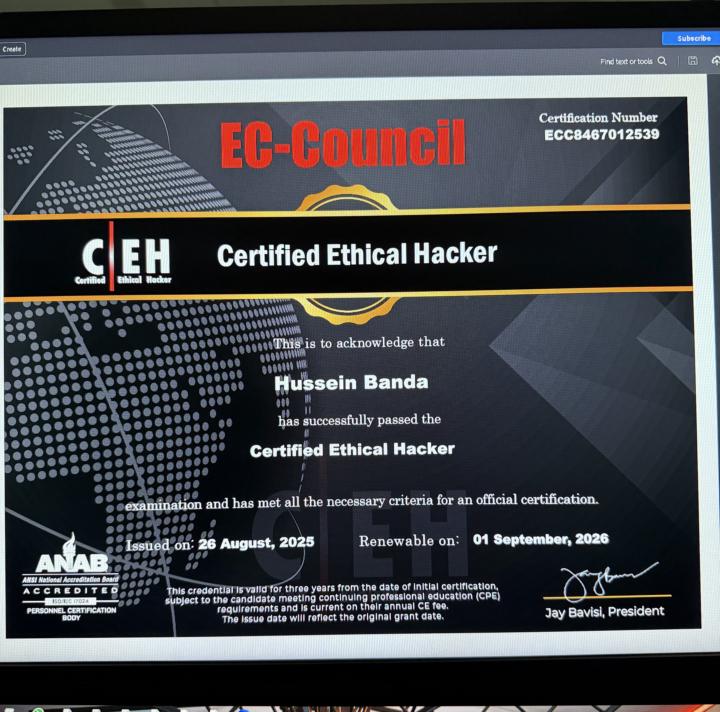
Certified Ethical Hacker
Am happy to share that I finally cleared my CEH exam a few months back . Now preparing for the CEH master exam. Wish me luck 😁
CySA recorded?
Damn, something came up! Looks like I'm gonna miss the cohort. Will it be recorded?
1
0
Attacks on different layers?
How close am I by stating, computer-born cyber attacks are ultimately just attacking one of the 7 OSI layers. Now to be clear I'm not referring to outside-the-box, good ole social engineering. I'm referring to an attack that starts at a computer terminal or with an application. For example Cross-site scripting (XSS)=application layer attack (layer 7), TCP SYN Flood=transport layer attack (layer 4), SSL scripting=presentation layer attack (layer 6), or MitM (man in the middle) = session layer attack(layer 5). Or am I a total NOOB and should just go learn so more?
1-6 of 6
Active 16d ago
Joined Nov 26, 2025
Powered by



