Activity
Mon
Wed
Fri
Sun
Feb
Mar
Apr
May
Jun
Jul
Aug
Sep
Oct
Nov
Dec
Jan
What is this?
Less
More
Owned by Bobby
IT resources for home offices, small offices and small businesses that don't want or don't need dedicated IT Support.
Memberships
Business Builders Club
1.4k members • Free
Skoolers
188.1k members • Free
10 contributions to Fractional IT
What's your biggest IT frustration right now?
Quick poll I want to help with what actually matters to you. What's your biggest IT frustration right now? 🔒 Cybersecurity / feeling vulnerable 💾 Backups / disaster recovery 🔑 Passwords / access management 🐢 Slow computers / outdated hardware 💸 Too many subscriptions / software bloat Vote below and drop a comment if you want to add context. I'll use this to shape what we cover next.
Poll
1 member has voted
1
0
New Year - New Look
We Changed Our Name. Here's Why (And What's Coming) Some of you knew us as The IT Group. That name worked. But it didn't fit. Because we're not trying to be your IT department. We're not trying to replace your MSP. We're not here to charge you $2,000/month for someone to reset your password. We're here to give small business owners something that's never existed before: Fractional IT expertise, without the full-time cost. Same knowledge. Same protection. Same confidence the big companies have. At a price that makes sense for a business your size. So, the name had to change. Welcome to Fractional IT. Here's What's Happening in 2026 I'm going all-in on this community. That means structure. That means value. That means showing up consistently to help you protect your business, secure your data, and stop wasting time on tech that should just work. Here's the plan: 🆓 FREE — "The Lobby" You're already here. You get: - Access to the community - Weekly educational posts - A front-row seat to what's possible This isn't going away. But if you want more... 🔐 PAID — "The Inner Circle" This is for business owners who are serious about protecting their business and levelling up their tech game. What you get: - Biweekly LIVE group Q&A calls (ask me anything) - Full library of recorded calls - Templates, checklists, and SOPs (security audits, backup guides, vendor evaluation frameworks) - Post questions anytime — I respond within 48 hours - Huntress Antivirus INCLUDED (enterprise-grade protection, ~$60/year value, on me) Founder's Rate: $47/month First 25 members lock this in forever. After that? Price goes to $97/month. You're not just paying for access. You're paying for peace of mind. 🚀 PREMIUM — "Fractional CTO" This is the closest thing to having me on your team without putting me on payroll. Everything in The Inner Circle, plus: - Weekly group strategy calls - Priority response — 24 hours max - Quarterly "Stack Audit" — I review every tool you're using and tell you what to keep, cut, and upgrade - Direct access to me via DM
1
0
Starter Pack - Downloads Here:
Most business owners, office managers, and practice administrators don’t think about IT until something breaks. That’s the worst time to figure it out. These downloads are the cheat codes. They show you exactly what to do when “that” scenario happens, whether it’s downtime, security, or the random tech chaos that halts your business. Use them to make decisions faster, avoid costly mistakes, and know you’re covered when the unexpected hits. No theory. Just plug-and-play resources you can actually use. (.docx files so you can edit as needed)
Microsoft Teams Calls being spoofed ???
Don't Get Fooled by Fake Teams Calls That Microsoft Teams call popping up on your screen might not be who it claims to be. A growing attack method targets small businesses directly through Teams, no email phishing required. Attackers impersonate IT support, vendors, or even Microsoft itself to gain remote access to your systems. If you're managing your own IT, you need to know how this works and how to shut it down. How the Attack Works The attacker creates a Microsoft 365 tenant with a display name like "Microsoft Technical Support" or "IT Help Desk." They then initiate a Teams call or chat to your organization. Because Teams allows external communication by default, the call appears legitimate. Once connected, they'll claim there's a security issue, an expiring license, or some urgent problem requiring immediate action. The goal is always the same: get you to grant remote access through Quick Assist, AnyDesk, or screen sharing—or trick you into revealing credentials. Some attackers flood your inbox with spam first, then call pretending to help you fix the "problem" they created. Why Small Businesses Are Prime Targets Larger organizations have IT teams who recognize these tactics immediately. When you're handling IT yourself, you might not have encountered this before. Attackers know this and specifically target smaller operations where a business owner or office manager might take the call thinking it's legitimate support. Your Defense Checklist Lock down external access in Teams Admin Center: - Sign in at admin.teams.microsoft.com - Navigate to Users → External access - Change "People in my organization can communicate with Skype and Teams users outside my organization" to Off or limit it to specific trusted domains only - Under Guest access, review and restrict permissions Block external calls specifically: - In Teams Admin Center, go to Voice → Calling policies - Disable "Make private calls" for users who don't need external calling capability
1
0

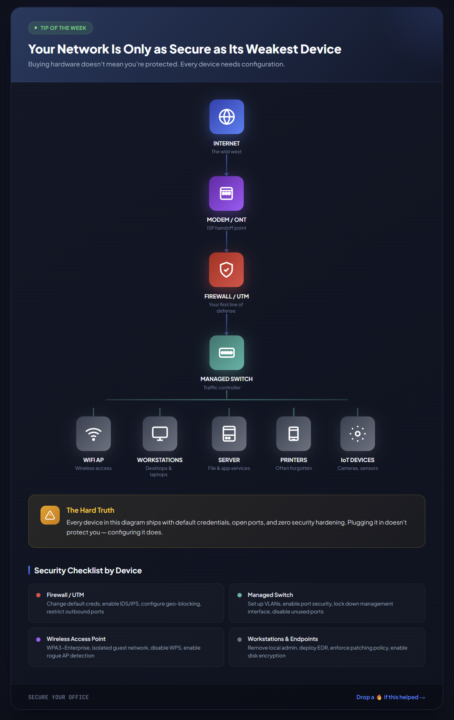
Your Network Is Only as Secure as Its Weakest Device
🔒 TIP OF THE WEEK: Your Network Is Only as Secure as Its Weakest Device Here's something most small business owners don't realize: Buying network equipment doesn't mean you're protected. That firewall you just installed? It shipped with default credentials (admin/admin), all outbound ports open, and zero threat detection enabled. That shiny new WiFi access point? WPS is on, there's no guest isolation, and it's broadcasting on the same network as your accounting server. What Every Office Network Should Look Like I put together a visual showing the basic flow of a properly structured network: Internet → Modem/ONT → Firewall → Switch → Endpoints Your endpoints branch off from the switch: WiFi access points, workstations, servers, printers, and IoT devices (cameras, sensors, etc.) Simple enough. But here's the catch: every single one of those devices needs specific security hardening. Quick Security Checklist by Device 🔴 Firewall / UTM - Change default credentials immediately - Enable IDS/IPS (Intrusion Detection/Prevention) - Configure geo-blocking for countries you don't do business with - Restrict outbound ports (block everything except what's needed) 🟢 Managed Switch - Set up VLANs (separate guest, IoT, and production traffic) - Enable port security - Lock down the management interface - Disable unused ports 🟣 Wireless Access Point - WPA3-Enterprise if possible, WPA2-Enterprise minimum - Create an isolated guest network - Disable WPS (it's a known vulnerability) - Enable rogue AP detection ⚫ Workstations & Endpoints - Remove local admin rights from daily users - Deploy EDR (Endpoint Detection & Response) - Enforce automatic patching - Enable disk encryption (BitLocker, FileVault) ⚫ Printers & IoT - Change default passwords (yes, printers have admin panels) - Update firmware regularly - Isolate on their own VLAN - Disable unnecessary protocols (FTP, Telnet, SNMP v1/v2) The Bottom Line Network security isn't a product you buy. It's a process you implement.
1
0
1-10 of 10
@bobby-boykin-1296
Founder @ FIRN Services | Making IT simple, strategic & growth-focused. I help private healthcare practices stay secure with super-smart tech stuff.
Active 10h ago
Joined Aug 19, 2025
ENFJ
Fort Worth, TX
Powered by

